Penetration Testing: Definition, Phases and Types
What is Penetration Testing?
A simulated cyber attack performed on a computer system to check for exploitable vulnerabilities is called penetration testing or simply pen testing. Through regular penetration testing, we can discover new vulnerabilities in the system that are missed or omitted during a vulnerability assessment. Also, this helps the organization to set up a more secure computer and network system in the working ecosystem.
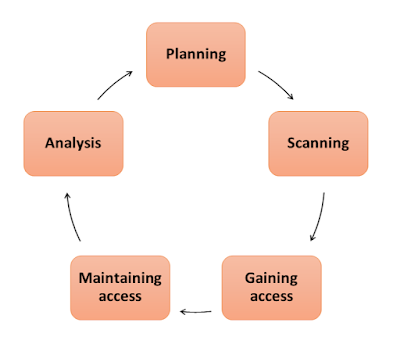
Phases of penetration testing
1. Planning and Reconnaissance
This phase includes gathering information about the target system through public and private sources like networks, domain names, mail servers, etc. This helps the pen testers to get preliminary information about the target system.
2. Scanning
In this phase, pen testers use various tools to examine the target system vulnerabilities. Pen testers can scan the application's code in a running state and how it behaves during testing.
3. Gaining access
In this phase, pen testers use web application attacks such as XSS attacks, SQL injection, etc. to unmask target vulnerabilities. Testers then try to exploit these vulnerabilities by stealing data, intercepting traffic, deleting data, or simply damaging systems applications.
4. Maintaining access
After gaining access to the system, pen testers maintain this access in this phase to accomplish their goals of exfiltrating data, modifying it, abusing functionality, etc.
5. Analysis
The results of the penetration testing are finally compiled into a report stating the exploited vulnerabilities, sensitive data breached and the amount of time the pen tester was able to remove the vulnerabilities from the system.
Types of Penetration Testing
1. Web Testing
In this penetration testing, web application vulnerabilities are exploited and security gaps are checked.
2. Network Testing
In this type of penetration testing, vulnerabilities in public and private networks are exploited. This can happen due to SSL certificate issues, HTTP protocol, etc.
3. IoT Testing
In this type of penetration testing, vulnerabilities in various IoT devices like T.V, A.C, etc are exploited.
4. Cloud Testing
In this type of penetration testing, vulnerabilities in cloud servers and workstations are exploited through remote access.